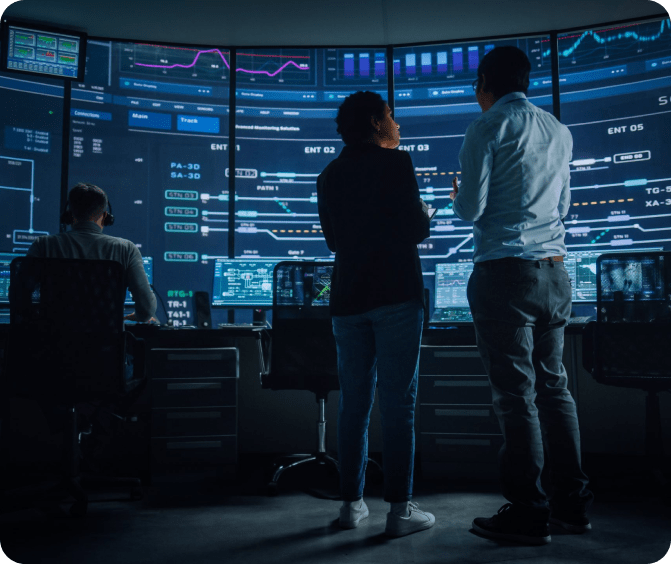
Mobile Surveillance Trailers
Preventing crime before it happens. Our Solar and Generator Powered crime prevention mobile surveillance trailers are designed for rapid deployment and are fully customizable to integrate with most any existing security system.
About Us
Welcome to Infinite Protection LTD, where safeguarding lives, assets, and revenues is not just a commitment but a calling.

Our mission is to Protect people, property and profits for companies across the United States. At Infinite Protection LTD, we bring together a team of seasoned professionals with years of combined experience in law enforcement, cyber crimes, and military service. This diverse expertise enables us to offer integrated security solutions tailored to your unique needs. What sets us apart is our holistic approach to security. We understand that every client is unique, facing distinct threats and vulnerabilities. That’s why we offer integrated security solutions tailored precisely to your needs. Whether you require mobile surveillance trailers, cyber defense strategies, or on-the-ground security personnel, we have the resources and the expertise to deliver results.


01
Crime Prevention Technology
In the past, mobile surveillance trailers could capture the crime so an investigation could ensue. How about preventing the crime before it ever takes place? Our Scouts offer crime prevention technologies, such as visual gun detection, gunshot detection, facial recognition and license plate recognition to help prevent the loss of property, profit or even life.
These Solar and Generator Powered surveillance trailers come equipped with complete turnkey solutions and are custom built to fit your needs.
02
Community Safety
Every day, your business faces security threats that cost you money and possibly your reputation. Keeping your company safe from external & internal threats can feel overwhelming and you may not know if your current solutions are enough.
As security experts, we understand that even one breach can cripple your business. At Infinite Protection, our team of former law enforcement professionals are dedicated to keeping your business safe and operational. With over 20 years of experience, you can be confident your business is protected from digital and physical security threats.
03
About The Scout
The Scout has become one of the most talked about Crime Prevention Surveillance Trailers on the market. This unit utilizes the latest Scouting Technologies to help prevent crime without the loss of property, profit or even life.
With violent crime on the rise across America, The Scout can be customized to fit any scenario. From Facial Recognition, License Plate Recognition to Visual Gun Detection and Gunshot Detection Technologies, The Scout is the answer for the security of any High School or College Campus, Public Event or simply as a Community Watchdog.
Now is the perfect time to add a Scout to your safety and security game plan. Combined with its low cost and available financing options, The Scout has never been more affordable!
Security
Security Integration Options
Area Security
Keeping areas safe and secure is a priority for any business or organization. From retail stores to schools, it’s essential to look at potential threats and how to mitigate them. With the right security measures in place, you can protect your property and people from harm.

Deployable Surveillance
Surveillance technologies have come a long way in the past few years. From stationary surveillance cameras to deployable surveillance solutions, we now have the capability to monitor and protect our premises from potential threats.

Drone Surveillance
Drone surveillance technology has been on the rise in recent years, giving businesses and individuals the power to monitor their environment with ease. Drone surveillance is a powerful tool that can help reduce theft, increase safety, and monitor performance.

Thermal Imaging
Thermal imaging is a technology used to detect and capture images of heat radiation emitted by objects, people, animals, or other sources in the environment. It works by using a special camera that can detect and visualize the infrared radiation emitted by objects, which is invisible to the human eye.

Smoke/Fire Alert
Fire can break out at any given moment and without warning. The fear of being injured or even killed by the intense flames or from heavy smoke inhalation is very real/frightening/present. A reliable alert system can mean the difference between life and death.
License Plate Recognition
Our LPR analytics automatically reads license plate information from vehicles, linking it to live and recorded video. This enables security operators to search and quickly find specific captured license plate video for verification and investigation.

Options
What's Available?
- Built to order (custom or turnkey)
- 3-year bumper-to-bumper warranty
- Several trailer colors available
- 360-degree discreet surround view
- Hydraulic and Electric Mast Options
- Works with most VMS
- Solar panels will charge even if shattered
- Easy and affordable to expand coverage
- Solar powered
- Gas or Diesel Generator Options
- AI Features
- Real-time live view
- 4-day autonomy
- Free training
- Sensor Integration

Order
Custom Orders Available
Custom orders are a service that allows customers to customize their orders based on their specific needs and preferences. Customers can choose from a wide range of materials, features and other specifications that can be tailored to their exact specifications. The service also offers an array of delivery and payment options, allowing customers to get their custom order faster and more conveniently.
Turnkey solutions are ready-made packages of products, services and support that can be quickly deployed to solve a problem or meet a need. They are often used to provide an “infinite” solution with minimal setup time and effort.
The type of scout surveillance hardware you choose will depend on the specific application and budget. Some options include surveillance cameras, motion sensors, audio recorders, access control systems, facial recognition software, and GPS tracking devices.
Process
What’s Our Process
Experience firsthand the efficiency and reliability of The Scout in real-world situations.
Demo the Scout
Select the model of scout you want to demo. Tell us what features are important. We will setup an onsite or online demo at no charge.
Building your scout
After having the opportunity to test a unit in real-life public scenarios, let's build The Scout that is just right for you.
Delivery and training
In 6-8 weeks after your custom design has been accepted your scout build will be complete. We will arrange delivery and free training.
f.a.q
frequently Asked Questions
What is Integration?
Infinite Protection specializes in delivering tailored solutions for mobile surveillance trailers, leveraging cutting-edge AI (Artificial Intelligence), robotics, and advanced analytics to ensure customers receive precisely what they need. Our comprehensive platform seamlessly integrates intelligent video analytics, mobile connectivity, and customizable automation features to enhance security while minimizing costs and operational complexity.
With Infinite Protection, customers benefit from real-time detection and response capabilities, empowering them to proactively address security events as they occur. Our platform also provides intuitive data organization and presentation tools, enabling swift and well-informed decision-making processes.
By aggregating data from various sources and systems, Infinite Protection optimizes data analysis and automates previously manual processes, allowing customers to focus their resources more effectively. Our user-friendly software is easy to deploy and adaptable to evolving needs, ensuring a seamless experience for customers throughout their operations.
Furthermore, Infinite Protection’s integration with mobile surveillance trailers enhances the value of existing systems, enabling customers to safeguard their assets and facilities more efficiently. Our solution enhances security, prevents losses, and improves operational efficiency, delivering tangible benefits for our customers’ peace of mind and business success.
Imagine the Possibilities
Imagine a system that no longer needs a security guard to physically watch every camera, monitor or sensor so you can catch improper behavior or initiate actions when an incident occurs.Imagine a platform that integrates all your security and business systems — from fire and water sensors to access cards and infrared detection.Imagine a system that’s intelligent enough to interpret people, actions and events and enforces fast, automatic actions when necessary. A system that helps employees become more efficient, more vigilant, and more effective in reducing and preventing fraud, vandalism, accidents and other issues.Imagine all this…with extreme simplicity, flexibility and scalability.

Reviews
Our Happy Clients

Great customer service and support!!! I have been using their CRM for awhile now and love all the different features! Not to mention how easy everything is to use! If you are looking for a way to manage and grow your business you need their CRM!!!
Kristina W.

I was looking to scale up my business and have the ability for more free time . To focus on what I need to and our partnership allowed me to do that.
Anthony

Loved this service excellent customer service
Austin R.

This was really informative for me and I can’t wait to put this great info to use when I get back home!
Luke Z.

Well spoken and very professional. Definitely taught me a few things.
Jason B.

Attended a training session. I was very impressed with the professionalism, knowledge, and experience provided.
Andy S.

Awesome instructors
Bruno F.
-Head Of Idea

Very informative and thought provoking, will definitely help in business building
Kristen F.
-Head Of Idea

Great presentation tonight. It’s good hear advice from individuals who’s determination and hard work has resulted in success. The entire team is awesome and they are all very knowledgeable. Issac was spot on on his advice and tips for creating and running a business that is going to be profitable. Thanks again!
Natalie G.

As a retired police officer, I believe that these scouts are extremely advanced surveillance systems. It would have been incredible to have even just a few of them spread throughout the city during my time on the force, I am certain that our crime rate would have significantly decreased with this technology. I strongly recommend […]
Melissa L.
-Head Of Idea

Well spoken and very professional. Definitely taught me a few things.
Jason B.

Very motivational and informative! They gave great, solid rules for success.
Luke G.
-Head Of Idea
Blogs
Latest Blog & Article
Discover the latest insights and articles on mobile surveillance. Stay informed with our newest blog posts.